Gossip Rant Chat Wa gwan Breaking Scandal Hot off the press Bulletin Dispatches Nachrichten

5G: Securing the next generation of mobile connectivity
The Winter Olympics in PyeongChang not only demonstrated a global level of athletic excellence, we also saw the world’s first Broad-Scale 5G Trial Service. Through 5G-connected tablets, select members of the audience were able to view individual competitors’ performances with real-time HD video and scintillating light-shows using connected lightbulbs were precisely controlled using the 5G trial network.

These applications of emerging 5G networks clearly demonstrate the underpinning ambitions for the technology; higher-bandwidth available on demand for data-hungry applications, and the proliferation of connected devices in a smaller geographical area. However laudable and desirable these goals are, 5G will also present new security challenges for enterprises, MNOs and device manufacturers as the technology reaches the market.

New network openness leads to new Vectors of cyber-attack
The new 5G technology is built on three ‘planes’ of architecture:
The Access: Used when devices move between networks, be that other 5G networks or WiFi data networks
The Forwarding: The part of the network architecture that governs how arriving packets of data are dealt with
The Control: The part of the network responsible for managing mobility and quality of service.
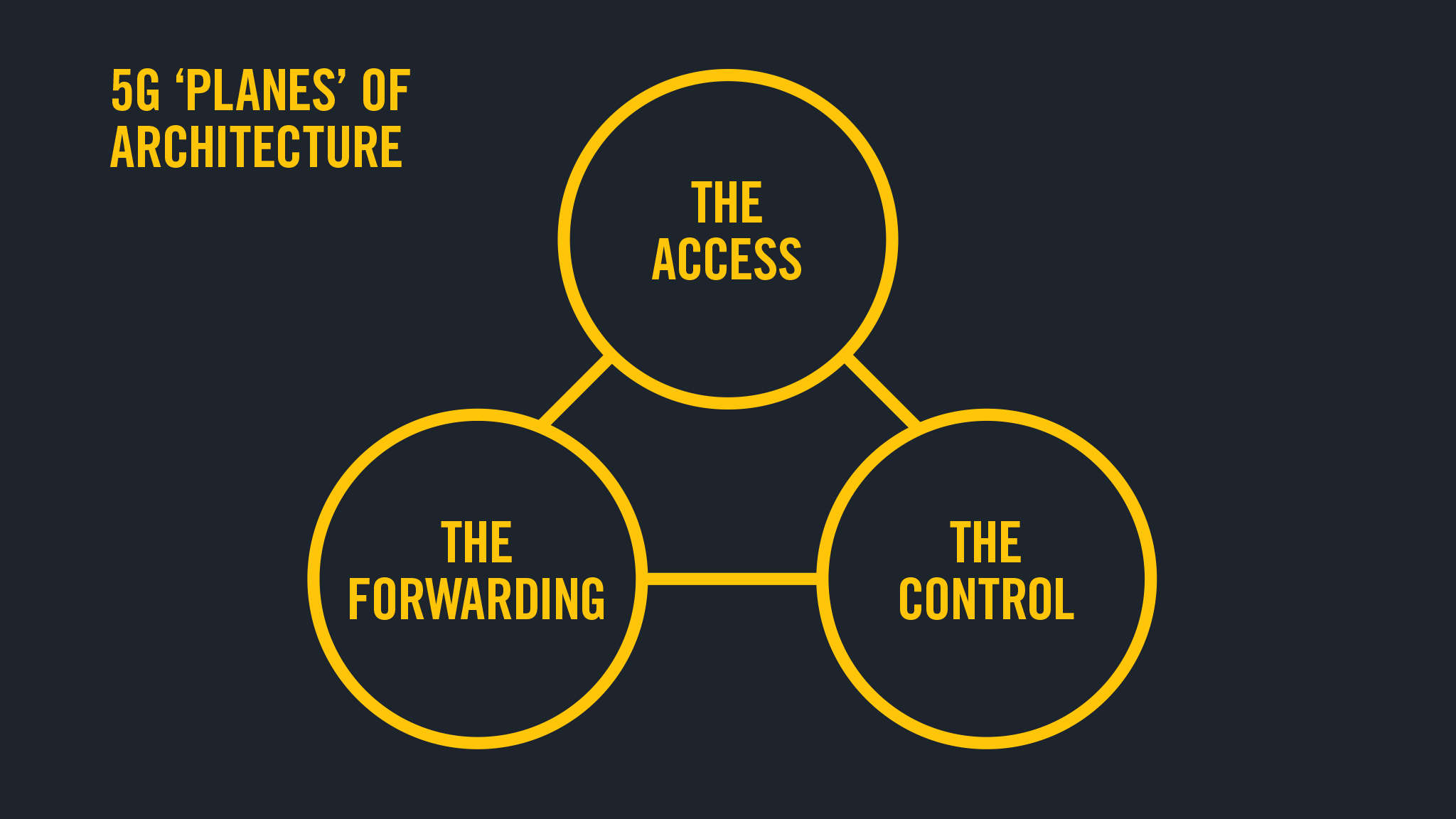
This network setup is broadly similar to 4G and other wireless/cloud-based networks, and in the last few years we have seen hackers attacking the control plane to recover user information. The control plane can be used to determine user location and can be used to push files to devices – a tempting target for hackers. With 5G, the intention is to open these control planes, enabling new operators to deliver services to their users. These operators will have little experience delivering services to third parties, so the need for robust security will be paramount. AdaptiveMobile Chief Strategy Officer Simeon Coney says; “We have started to see attacks on these planes in the last couple of years, to look up users without their permission. They are not expensive to perform. The danger is an inherent widespread weakness creating a botnet.”

More devices, more vulnerabilities
With increasing numbers of devices come increasing vulnerabilities. 5G is designed to support both high-bandwidth connections for intensive applications and lower bandwidths available to multiple devices in a smaller area – ideal for connected smart devices and the IoT industries. Forecasts from Gartner indicate that, by 2020 (the predicted date for the beginnings of commercial 5G availability) the IoT market will consist of more than 20 billion connected devices and be worth more than $3 trillion USD. This proliferation, across multiple markets, multiple manufacturers and multiple operators will lead to increased vulnerabilities, especially as the trend for connected devices is integration. Embedded, low power sensors in street lights, for example, may last for years and be difficult to update as new security concerns come to light.
Increasing bandwidth enables new technologies
The Winter Olympics showed us that 5G is capable of data transfer at incredible speeds, and the commercial specification requirements show that these speeds will be in consumers hands. 5G will give users less than 1ms latency and up to 10Gbps – an improvement of between 10 – 100 times beyond the capabilities of current 4G and LTE networks. This step-change in data speeds will enable new mobile technologies for users- each with their own security risks. 3D virtual reality applications, HD and 4K mobile video streaming and rich-data GIS systems will become more commonplace. These new to mobile implementations will require robust end-to-end security designed and ready to go for day one of 5G launch.